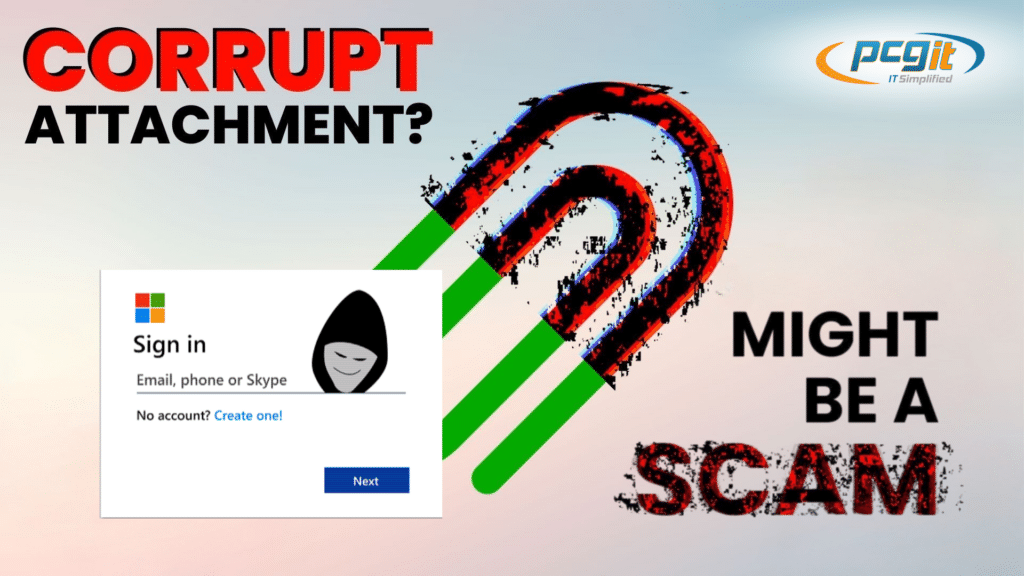
Beware of Corrupted Email Attachments: It Could Be a Scam
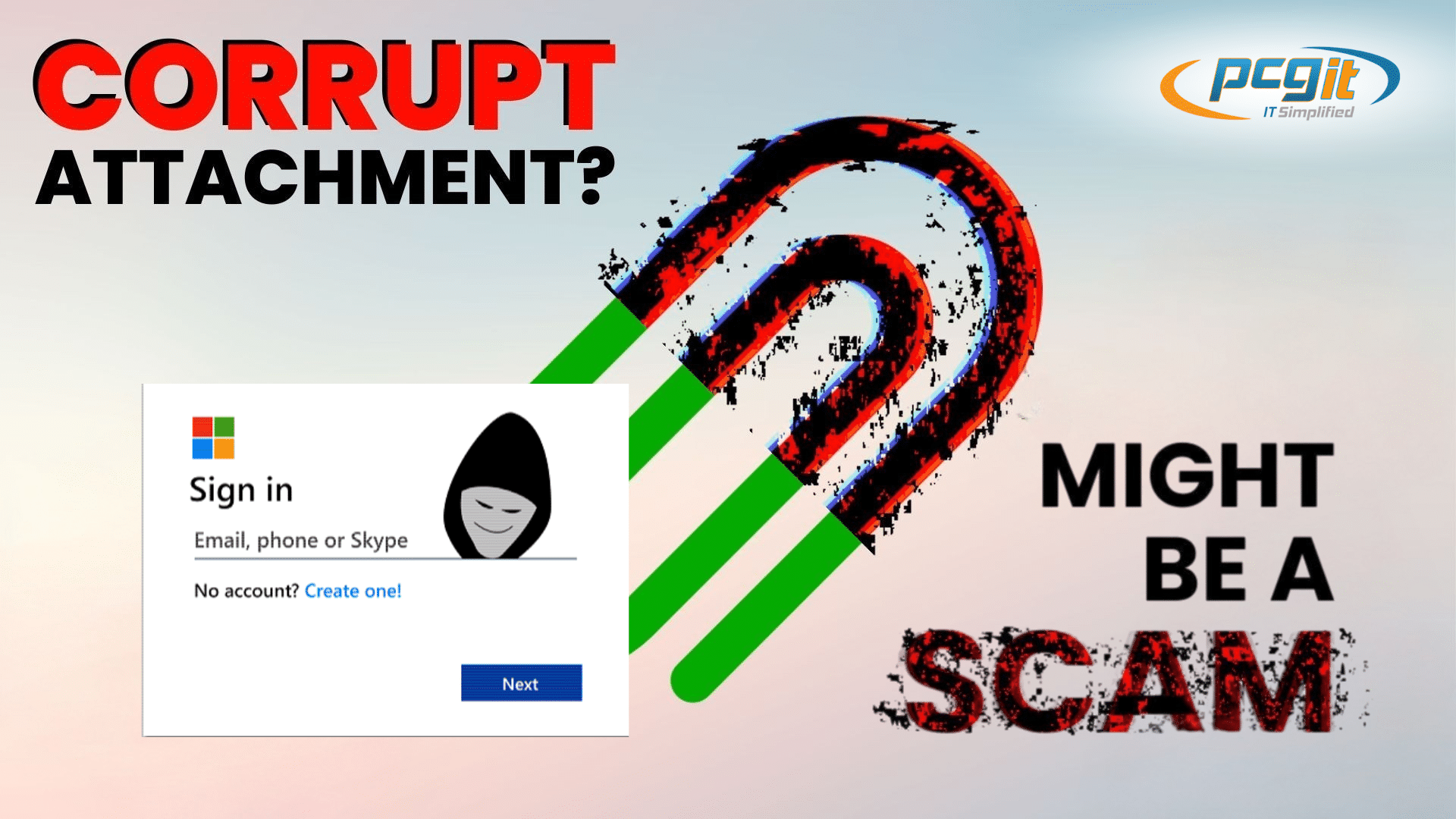
In today’s fast-paced business environment, email has become the primary mode of communication. We routinely open emails from colleagues, clients, suppliers, and partners, often without a second thought. But have you ever stopped to think twice before opening an email attachment? A simple Word document could be the gateway to a scam that threatens your business’s cybersecurity.
The New Threat: Corrupted Email Attachments
Scammers are constantly evolving their tactics, and one of their latest tricks is the use of corrupted Microsoft Word files. At first glance, everything seems normal. You receive an email with an attachment that looks legitimate—maybe it’s an invoice, a report from a supplier, or even a colleague sending over some documents. You open it up, and Word asks to repair the file. You click “repair,” and that’s when things go south.
This repair process isn’t about fixing the document. Instead, it’s a sneaky way of bypassing email security filters. While most security filters can detect malware in attachments, corrupted files often slip through undetected because they can’t be analyzed properly. When you click to “repair” the file, you’re unknowingly allowing malicious content to enter your system.
The Word document may look fine, but hidden within it could be a malicious QR code or link that takes you to a fake login page—usually a fraudulent Microsoft 365 login screen. If you enter your details, hackers gain access to your account, and with it, the potential to steal sensitive business data, lock you out of essential files, or even hijack your email account to launch further phishing attempts.
Why Phishing Attacks Are So Dangerous
Phishing is a type of cybercrime in which scammers trick victims into giving away sensitive information like passwords, bank details, or login credentials. It’s a method they’ve perfected over the years, evolving into more sophisticated attacks that are harder to detect.
In the past, phishing scams typically involved email attachments or links that looked suspicious. Today, however, these attacks are more complex and harder to distinguish from legitimate emails. Scammers know how to craft emails that appear genuine, often mimicking trusted brands, banks, or even colleagues. The more authentic the email looks, the more likely you are to trust it—and that’s exactly what the attackers are counting on.
The Impact on Your Business
The consequences of falling victim to a phishing attack are far-reaching:
- Access to Sensitive Information: A single compromised login can give hackers access to cloud systems, customer databases, and other sensitive business information.
- Disruption to Operations: If scammers lock you out of essential files or systems, your business could come to a standstill, costing time and money.
- Financial Loss: Cybercriminals can siphon funds from your business accounts or initiate fraudulent transactions.
- Damage to Reputation: If your business’s data is compromised or if clients’ sensitive information is exposed, your reputation could be permanently damaged. Rebuilding trust can take years, and in some cases, it may never happen.
- Legal Ramifications: Depending on the nature of the breach and the information stolen, you may be legally liable for not taking adequate steps to protect your data.
How to Protect Yourself and Your Business
While the cyber threats continue to grow in sophistication, protecting yourself and your business doesn’t require an advanced degree in cybersecurity. The best defense is awareness and caution. Here are some steps you can take to safeguard your business:
1. Slow Down and Think Twice
It’s easy to open an attachment or click on a link without thinking. However, scammers often create a sense of urgency in their emails to get you to act quickly and without questioning the email’s authenticity. Always take a moment to pause before clicking.
2. Look Out for Red Flags
If an email seems too urgent or asks for sensitive information, be suspicious. Cybercriminals often use tactics like threatening language or “urgent” requests to provoke hasty actions.
3. Verify the Source
If you receive an unexpected email, even from someone you know, verify its legitimacy. Contact the sender directly—preferably by phone or through another method—before opening any attachments or clicking on links.
4. Avoid Trusting Attachments Just Because They Look Professional
A well-crafted email can be deceiving. Even if an email attachment looks professional or comes from a trusted source, it’s still important to verify before opening it. Scammers are getting better at mimicking legitimate emails and documents.
5. Educate Your Team
Phishing scams are not only a threat to you—they can also compromise your entire team. Educate your employees about how to recognize phishing attempts, the risks of corrupted attachments, and the importance of email security. Training your team to be cautious and vigilant can help prevent costly mistakes.
6. Use Multi-Factor Authentication (MFA)
Enable MFA on all accounts, especially those that store sensitive business information. MFA adds an extra layer of security, making it harder for hackers to gain access even if they manage to steal a password.
7. Keep Software Updated
Ensure your security software, email filters, and antivirus programs are always up to date. This will help protect against known threats and increase your ability to detect malicious files.
Email phishing attacks, particularly those involving corrupted attachments, are an evolving threat to businesses of all sizes. While cyber criminals are constantly coming up with new ways to breach security, the most effective defense is being cautious and vigilant.
By taking simple steps such as thinking before you click, verifying the legitimacy of emails, and educating your team, you can significantly reduce the chances of falling victim to these scams. Protecting your business requires proactive effort, but with the right mindset and security practices in place, you can stay one step ahead of cybercriminals.
If you’re unsure how to better protect your business or need help in improving your cybersecurity, don’t hesitate to reach out. We help businesses safeguard their data and avoid costly cyberattacks every day.